The past couple of years have seen a rise in software supply chain attacks, with the most salient example being the Solarwinds attack. As production environments have gained multiple layers of protection, and much of the attention of security teams, malicious actors have set their sights on “poisoning the well”, i.e., …
With extensive hands-on experience in cloud native security, we founded Darkbit to help organizations address security risks in their ever-growing and changing cloud environments. As the next chapter in our journey, we’re now joining forces with Aqua to realize this shared vision, helping deliver best in class …
With the move to cloud native development comes potentially increased risk of services that are exposed to the Internet and can easily be discovered by attackers. When combined with the fast pace of change in Kubernetes versions, there’s real risk of being one vulnerability away from a security incident. Recently I …
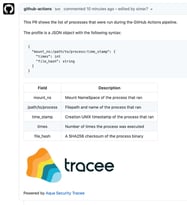
In my previous post, I covered how you can secure your CI/CD pipeline with Tracee from potentially malicious code executions. We’re now releasing Tracee GitHub Action, which makes using Tracee a plug-n-play experience and doesn’t require any prior knowledge of eBPF or Docker. We’re also introducing a new capability to …
In April, MITRE published the ATT&CK matrix for Containers covering adversarial techniques that target container technologies. At Aqua, we were proud to support this effort by sharing our knowledge and helping refine and extend the matrix. As for the risks in Kubernetes, Microsoft created a framework for Azure-based …
Insufficient access restrictions, permissive storage policies, and publicly exposed assets are only a few of the mistakes companies make when configuring their cloud infrastructure. The scale of the problem is mind-blowing, with 90% of organizations being vulnerable to security breaches due to cloud misconfigurations. …
Today, AWS announced the general availability of ECS Anywhere; a simple but powerful extension of AWS Elastic Container Service (ECS) to manage containers wherever they run – Aqua has been working closely with AWS to deliver a unified security experience for ECS Anywhere so enterprises can embrace the cloud native …
Tracee is an open source runtime security and forensics tool for Linux, built to address common Linux security issues. By leveraging the advantages of Linux extended Berkeley Packet Filter (eBPF) technology to trace systems and applications at runtime, Tracee analyzes collected events to detect suspicious behavioral …
When you’re operating Kubernetes clusters, an important area of focus is in ensuring your authorization model is correct and provides users with the least privileges needed for them to carry out their roles. As such, blanket cluster-admin privileges should never be used and in particular the in-built system:masters …
Anyone looking to improve the security posture of their cloud native applications knows that a vulnerability scanner is an important tool to add to the toolkit. Automating vulnerability scanning into your build pipeline can reduce the likelihood of successful attacks and help protect your containerized workloads. …
When it comes to containerized workloads, resolving the underlying image's security vulnerabilities is paramount to ensuring the safety of your environment. Getting security risk information into the hands of developers quickly and efficiently is key to keeping development cycles as short as possible while maintaining …