The cloud is fundamental for digital transformation, but for many organizations, a hybrid approach is preferred. This ideally allows you to use the very same foundational tools on-prem as your destination in the cloud. Well, now you can do just that with Amazon EKS-Distro (EKS-D), a new Kubernetes distribution that enables you to run the same secure, validated, and tested components that power Amazon EKS anywhere you want. We at Aqua have been working extensively with AWS to secure EKS-D and ensure that all the security controls we have for Kubernetes environments and workloads extend to this new distro.
EKS-D is a customer-managed solution packed with open-source goodness: patches for operational stability and security fixes, everything tested for compatibility with upstream Kubernetes, and all aligned with Amazon EKS.
Kubernetes complexity
Containers were introduced to produce lightweight, resource-optimized, and highly scalable applications. However, with Kubernetes at the helm, containers are now being used as building blocks to create more powerful and sophisticated microservices architectures. This shift in approach has moved complexity to the orchestrator layer, right in the sweet spot of Kubernetes. As a result, K8s has become the bread and butter of modernization and migration strategies, be it in the form of hybrid or multi-cloud architectures.
With EKS-D, AWS is doing the heavy-lifting of providing consistent and secure access to installable, reproducible builds of Kubernetes to fast-track application modernization. On the other hand, as your Kubernetes footprint grows into more complex architectures across diverse environments, it becomes increasingly challenging to manage efficiently — without compromising security.
Kubernetes comes with multiple nerd knobs that are so intricately woven into the infrastructure that even a small configuration change can have major consequences across your environment. Compounding this fact is that Kubernetes is still rapidly evolving with new features, so, managing these complexities can be time-consuming and overwhelming. Just as it seems like the knowledge gap is unsurmountable, Aqua comes to the rescue armed with our newly launched KSPM (Kubernetes Security Platform Management) to address all your Kubernetes security needs.
Holistic security for Kubernetes
Using our complete solution for Kubernetes security, you can protect entire clusters with agentless runtime security. And you can defend your Kubernetes workloads without requiring host OS access. This provides for seamless deployment on any managed or restricted K8s environment.
In addition, our Aqua KSPM solution delivers a comprehensive suite of capabilities that drives a whole new level of Kubernetes infrastructure security. It’s a pioneering approach to effectively tackle misconfigurations, obscured visibility, security best practice knowledge gaps, enforcement of least privilege access, and the most accurate evaluation of workload security compliance.
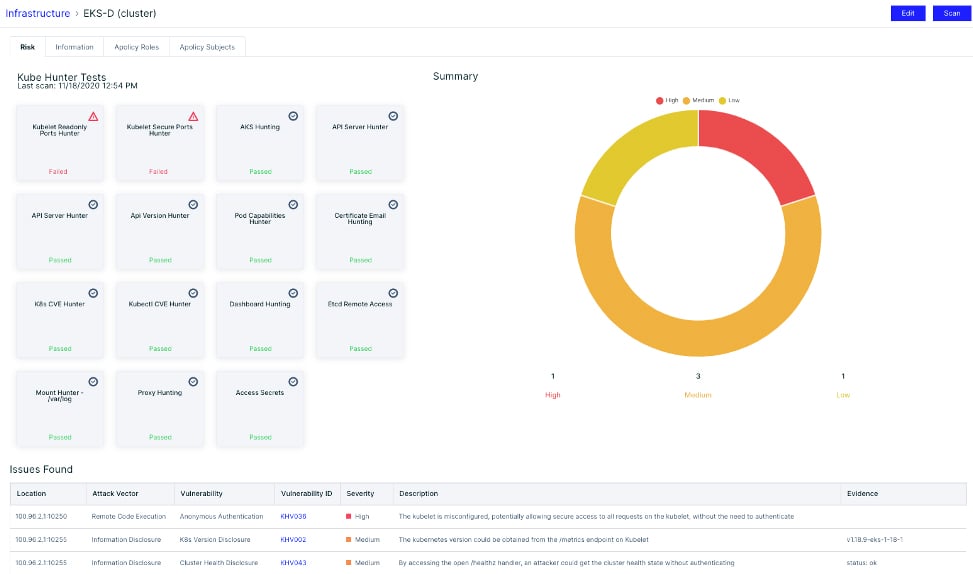
Risk Explorer - Aqua Risk Explorer performs automated discovery and risk assessment of the assets in your K8s environment while providing a single-pane-of-glass view across your cluster.
kube-bench - Aqua has long been a champion for cluster security via kube-bench, which automates the evaluation of a cluster against the CIS Benchmark. It is the de-facto standard within the open-source community and an intrinsic part of our Aqua Enterprise platform.
kube-hunter - Another open-source tool for Kubernetes security, kube-hunter is the industry’s only active pen-testing tool that hunts for security weaknesses in your Kubernetes clusters.
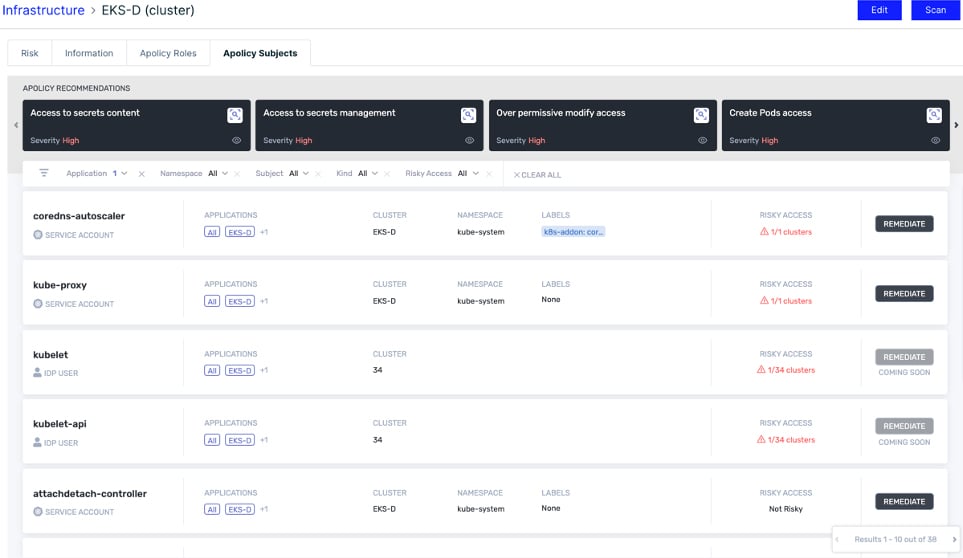
Roles and Subjects Risk Assessment - Aqua addresses least privilege security gaps by evaluating Kubernetes user and service account privileges for excessive permissions — and aids in their remediation.
Kubernetes Assurance Policies (KAP) - KAP is our newly launched Kubernetes-native capability to evaluate the security posture of your workload configuration. In conjunction with the image risk assessment, KAP evaluates Kubernetes pod configurations (e.g., resource limits, capabilities, networking) against security best practices to assess workload compliance.
Closing thoughts
You’d be hard-pressed to find success stories about Kubernetes that didn’t include a long list of lessons learned, and a common theme are K8s security challenges. At Aqua, all of our research and learnings about securing Kubernetes and other cloud-native environments have led to a comprehensive approach that secures both the Kubernetes infrastructure, as well as the workloads that run on it. The availability of Amazon EKS-D as an open source K8s distro opens many possibilities for smooth hybrid deployments and, with Aqua, consistent protection across all environments.