Windows containers have recently been gaining a lot of popularity, especially in the delivery of .NET applications and SQL server containers. Aqua Security has been working diligently with the Google Cloud team to support the launch of the new Windows GKE. This allows Aqua users to secure their GKE deployments using both Windows and Linux containers, giving them single-pane-of-glass visibility, consistent controls, and unified policy management.
Security Considerations When Using Windows Containers
OS Version Compatibility
Microsoft offers two distinct runtime isolation modes for Windows containers. Currently, Windows GKE only supports process-isolated containers, also called Windows Server containers. Process isolation allows multiple containers to share the underlying kernel with each other and with the host, but unlike Linux, Windows containers need access to the same syscall-DLLs that the host OS uses. As a result, you’ll need to maintain version compatibility between the container image and the host OS running in your GKE Windows node pool. For major security updates, your application images should follow the same patching cadence as the Microsoft base images.
Base Image Security Challenges
Even Microsoft's smallest Windows Server image, called Nanoserver, still has a sizeable attack surface that can be used to exploit OS vulnerabilities and gain privileges on the host OS, making other applications that share the same kernel susceptible to exploits. There is no FROM scratch option in Windows, which means that you'll need to start from a base Windows image.
Aqua Cloud Native Security Platform shares a multitude of integrations with Google Cloud Platform services across the application lifecycle, securing GKE workloads running on both Linux and Windows. Aqua uniformly secures the varied and heterogeneous GCP Kubernetes workloads by providing a unified view of your security posture.
Here’s a glimpse into a few of Aqua’s capabilities on Windows GKE:
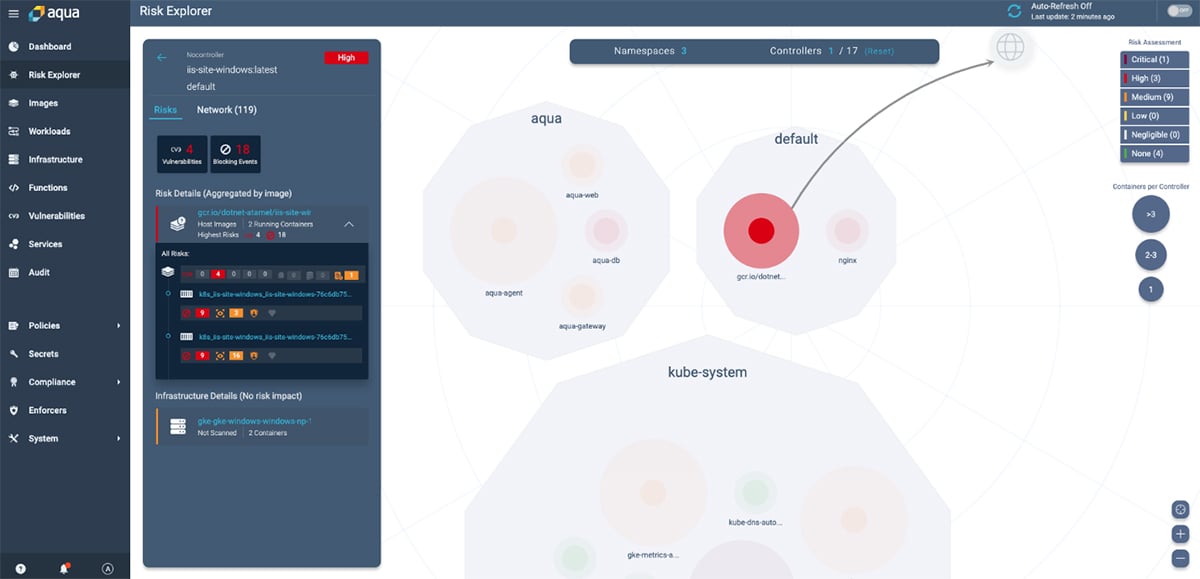
Vulnerability Scanning for Risk Assessment
This is a preliminary step in understanding the security posture of your environment. Aqua performs risk assessment throughout the application deployment lifecycle and produces a prioritized list of known vulnerabilities tailored specifically to the impact on your environment. Aqua also provides security expertise and remediation advice based on a structured decision workflow: Remediate, Mitigate, or Accept. You can read more about it in our vulnerability management best practices blog post.
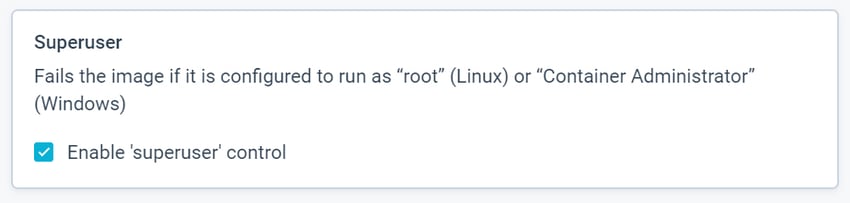
Assurance Policies for Image Compliance
Assurance policies are actionable controls that enable you to create compliance gates per your security tolerance. Aqua CSP provides a security hook to sanitize the image build pipelines, evaluating them against your Assurance policies. For example, you can choose which approved Windows base images to allow in runtime, preventing any version mismatch issues. You can also restrict the attack surface by blocking containers from running with "Container Administrator” privileges.
Runtime Security Enforcement
Aqua CSP provides \ runtime policy controls that automatically prevent many types of malicious activity and container-related attacks in real-time. Runtime policies can be applied in Audit as well as Enforce mode. For example, you can block non-compliant images from running in your environment, employ a file-block or blacklist certain executables.
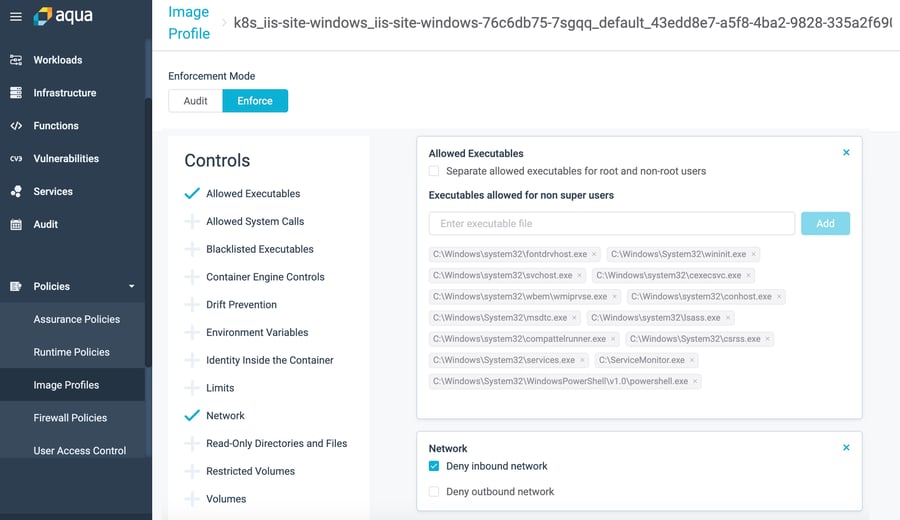
Image Profiling for Behavioral Whitelisting
While Assurance policies allow you to quantify risk and set your compliance rules, Image profiling takes a different approach called behavioral whitelisting. After observing the container behavior and setting a baseline, it employs whitelisting to allow only permitted, observed behaviors to execute, with granularity that can stop specific processes, executables, files, network connections, syscalls, or volume mounts.
In the screenshot below you can see that Aqua has profiled all the executables and network traffic pertaining to the IIS-server windows workload and those being whitelisted.
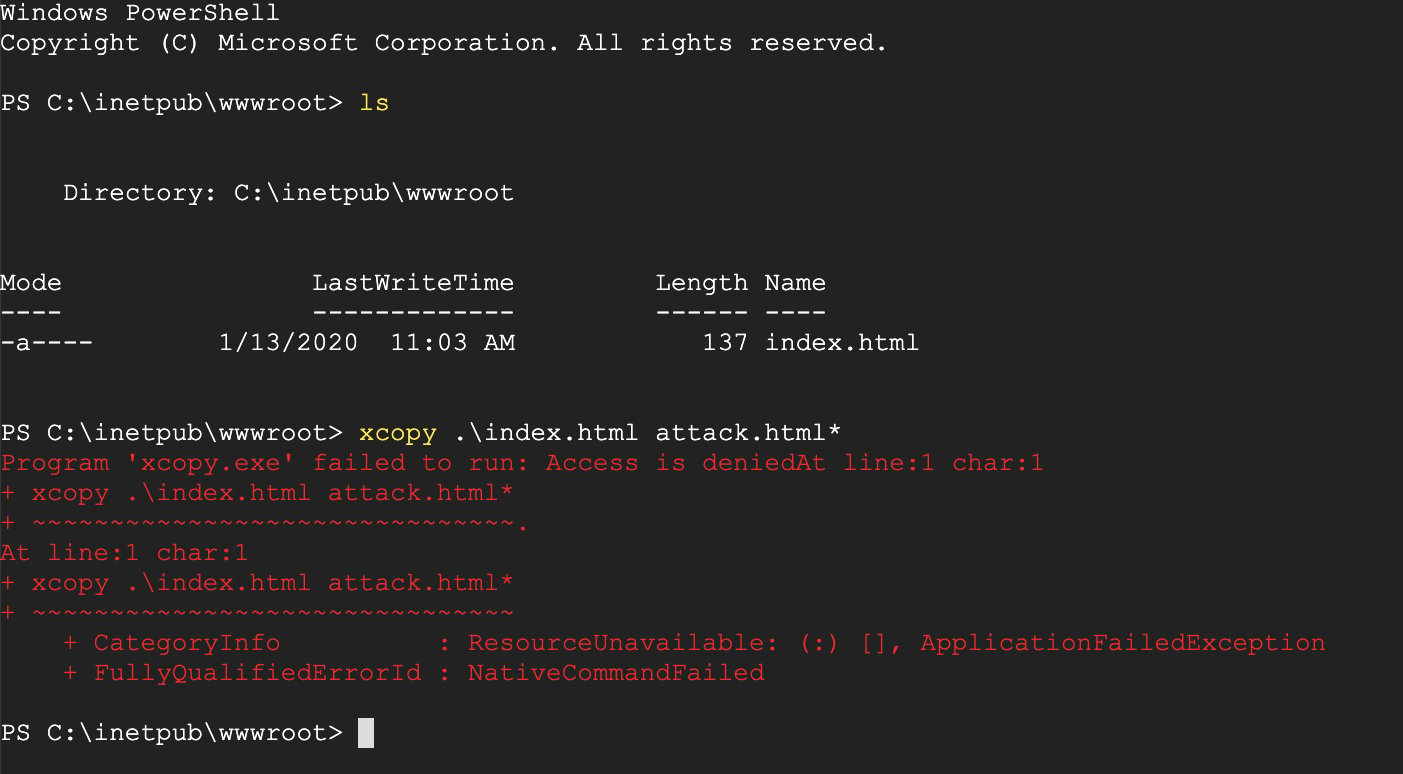
The screenshot below shows that the xcopy command is being blocked by Aqua, as it is not whitelisted by the image profile.
Using GKE Securely in Heterogeneous Environments
Aqua’s native integration with Google Kubernetes Engine (GKE) empowers enterprises to make use of modern application development and deployment methodologies while improving their overall security posture – all with no impact on developer agility or workload performance.
In a world of mixed-OS Kubernetes clusters, running your Linux and Windows workloads side by side comes with its unique challenges. Windows GKE provides users with a consistent way to manage their heterogeneous container workloads for a truly hybrid experience. Irrespective of the differences between the Linux and Windows containers, the underlying security principles and attack tactics remain unchanged. Aqua CSP rises to the challenge of providing seamless security controls for all your cloud-native security needs for a truly secure hybrid experience.
To learn more, please check out Aqua CSP on GKE.
Try Aqua at the GCP Marketplace and only pay for what you use in the PAYG model.