On Monday, “day 0” of this year’s KubeCon/CloudNativeCon, we held our first KubeSec Enterprise Summit event, co-located with KubeCon under the auspices of the CNCF. Aqua hosted the event together with our partners Red Hat and AWS. The event was over-subscribed, and we had to make special allowance for late registrants, bringing our Seattle Convention Center hall to capacity with standing room only and more than 280 participants – most of whom were there for the entire 9 to 5 schedule!

As Kubernetes adoption is hitting a critical inflection point, more and more organizations in the Global 1000 are adopting it and beginning to move applications into production. We felt it was time for an enterprise-focused event to shed some light on the experiences and best practices that both early adopters and key technology players in the industry can share.
Speaker Highlights
Our focus at KubeSec Summit was on sharing end-user experiences and best practices, and we had an excellent lineup of speakers from organizations such as JP Morgan Chase, Starbucks, and Tinder.
Oren Hamami from JPMC gave a great overview of the steps that large organizations must take to manage the process of securing cloud native applications at scale, while the Starbucks and Tinder presentations were more specific in focusing on specific aspects of security – networking and RBAC, respectively.

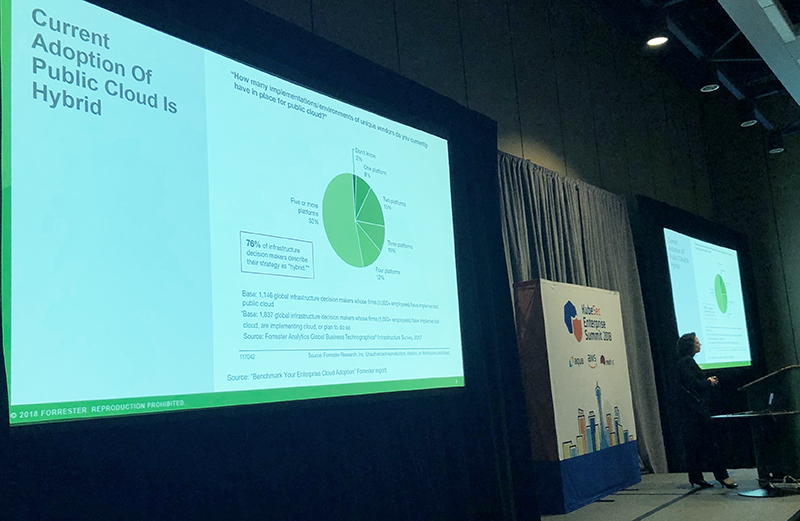
Amy DeMartine from Forrester Research gave an insightful overview of the state of container security and DevSecOps, with special attention given to data on how multi-cloud deployments are already a reality in most enterprises.
Aqua’s Liz Rice and Red Hat’s Michael Hausenblas, the co-authors of the O’Reilly book on Kubernetes Security gave a rundown of key best practices
Sarah Young from Versent gave a lively “how to lose a container in 10 minutes” presentation, a reminder that crypto-currency mining is still the most popular abuse of unsecured K8s clusters.
There were also presentations by Aqua, Red Hat and AWS on best practices and the expanding toolset and features available both within the platforms (such as OpenShift), and cloud services that run Kubernetes, as well as enterprise-grade security platforms such as Aqua CSP.
We ended with a panel featuring the always insightful and sometimes acerbic Dan Walsh (“Mr. SELinux”) from Red Hat, Aqua’s VP of product strategy Tsvi Korren, and Sarah Young, where the importance of good defaults, and Kubernetes security misconceptions were highlighted.
Key Takeaways
In listening to the many great presentations, and garnering reactions from attendees, it’s clear that KubeSec was the right event at the right time. There’s a lot of healthy interest in securing cloud native applications and the experience of early adopters is very valuable. A few key observations emerge:
Understanding of the importance of embedding security into the process: As cloud native apps change not just the technology but also the process of developing and delivering applications, it’s evident that organizations understand that security must be embedded into this process as early as possible. Perhaps for the first time in the history of enterprise IT, security is not bolted onto runtime environments as an afterthought, but implemented into processes before organizations go into production. Yes, there are varying degrees of implementing this, from using open source tools to full-blown implementations of security controls and enforcement, but the realization of some form of DevSecOps is clearly catching on.
One size does not fit all: This repeated in various forms in several presentations. You cannot nor should attempt to do everything at once. Pick your battles, and phase your deployment while defining very clear boundaries of what you will address centrally, and what will be addressed by individual application teams. As organizations move beyond the single cluster, single app scope, a much more structured approach is needed. You can learn more about this topic from my “Cloud-Native Security at Scale: Multi-App, Multi-Cloud, Multi-Stack, Multi-Team” webinar that’s available on demand.
Automation is key: Automation is thematic to the cloud native world, and security cannot be an exception if it is to keep up. This isn’t just about automating the application of security controls, but also automating the service delivery itself, so that various teams can onboard themselves and consume security in the form of deployment templates, service APIs, policy definitions, reporting, etc. As JPMC put it, “everything must be consumable programmatically”.
Kubernetes as an infrastructure needs security: We obviously did not know this when planning the KubeSec event, but the fact that the most severe Kubernetes CVE to date was published the week before the event made sure that this “elephant in the room” was not ignored. It’s not that K8s is inherently more vulnerable than anything else, but it’s a complex piece of software that requires security scrutiny and defense in depth. The vulnerability was fixed quickly and responsibly, which is very reassuring, but it also served as a wake-up call to organizations who’ve been not paying enough attention to where and how their clusters are being deployed.
We’ve already set in motion our plans for a KubeSec summit at the 2019 KubeCon Europe event , so watch this space!

