Securing software supply chains requires strong governance and rich data, both to help ensure that only approved components are executed on production machines.
But how do you define what’s approved? And more importantly, how do you control this?
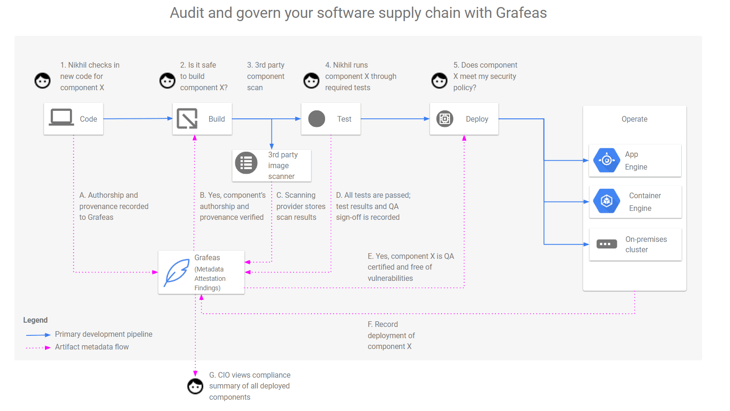
Today Aqua is pleased to announce support for Google Grafeas, released today - an open source initiative for auditing and governance of the modern software supply chain.
Grafeas defines the central source of truth for organizations that need to track and enforce policies across an ever growing set of software development teams and pipelines. Build, auditing and compliance tools can use the Grafeas API to store, query, and retrieve comprehensive metadata on software components of all kinds.
How does Aqua support Grafeas?
Aqua will support the Grafeas specification, so that Aqua’s image vulnerability results can be added to the metadata aggregated by Grafaes.
By integrating Aqua into the CI/CD pipeline, a user can trigger vulnerability scanning as part of a build process, allowing developers to get early feedback for security vulnerabilities that are found in the image. Aqua’s scan results are sent to Grafeas, allowing users to query the production environment for vulnerabilities in containers across the deployment.
In addition, Aqua will integrate with Grafeas as a source for metadata, allowing Aqua users to define deployment rules that are based on information stored in Grafeas.
For example: using the integration between Aqua and Grafeas you will be able to define a rule where only images that have a specific Grafeas note will be able to run in production. Aqua will enforce these rules using its Aqua Enforcer.
What about Manifesto?
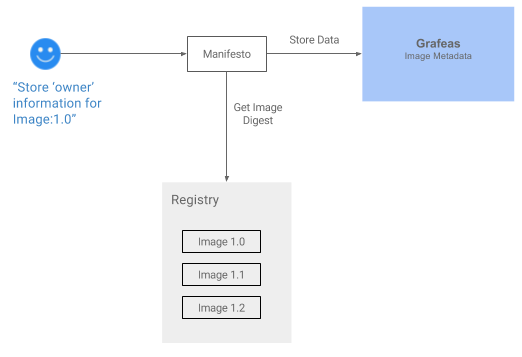
Manifesto is an open source initiative by Aqua for storing and querying metadata associated with container images. Users use Manifesto’s easy command line tool to add and manage any metadata information about an image, like the owner’s contact details, slack channel or usage information for the image.
For example, the following command assigns metadata information stored in a JSON file to the “myorg/imagetest” image:
$ ./manifesto put myorg/imagetest something ~/temp.json
By integrating Manifesto with Grafaes as a storage back-end users will be able to use Manifesto to store and query data against Grafaes!
To try Grafeas or to join the project, visit: https://github.com/grafeas

