Kubernetes Version 1.25 was released with 40 new enhancements including 13 Stable, 10 Beta, 15 Alpha, and 2 Deprecated. Join us as we present some of the notable features in this release, apply security with the Pod Security Admission (PSA), validate whether your cluster is using containerd, and give an overview of the features. These improvements span several sections (SIG) such as storage, auth, networking, security, and more.
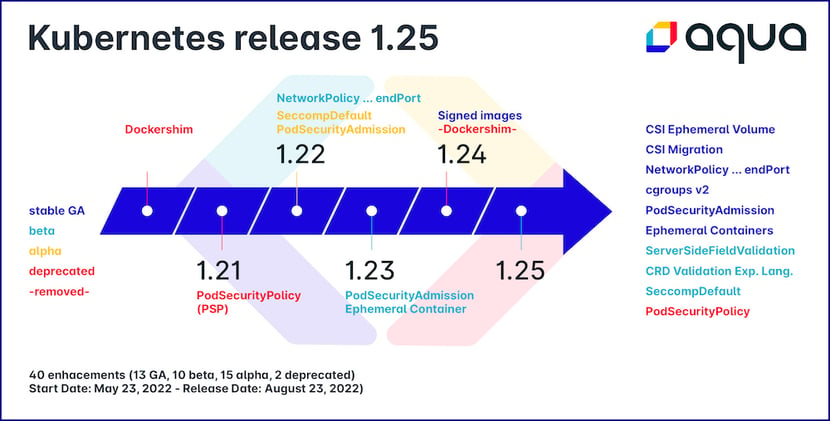 40 enhancements - Start Date: May 23, 2022 – Release Date: August 23, 2022
40 enhancements - Start Date: May 23, 2022 – Release Date: August 23, 2022
With PSP Removed, It’s Time to Use PSA
Designed to improve usability, you don’t need to know the security detail to apply apply the security standards. Pod Security Admission is an admission controller that evaluates Pods against the security controls (PSS) to admit or deny features in the pod.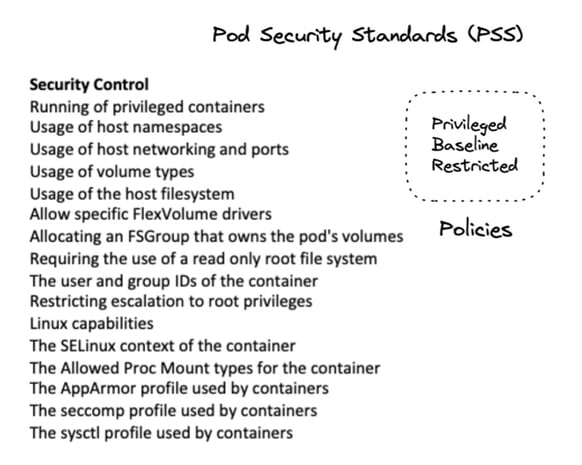
The Pod Security Standards (PSS) define 3 levels: privileged, baseline, and restricted, from very permissive with the privileged mode to a restricted mode that tries to apply the principle of least privilege in the pod.
The combination of these controls (see image) determines the security policies. For example, spec.ephemeralContainers[*].securityContext.runAsUser with the value RunAsAny would be one of the controls of the Privileged policy. You can find more about Pod Security Standards (PSS).

In PSA, security profiles are applied at the namespace level through labels
The PSA uses namespace labels for enforcement and can be configured in modes such as enforce, audit, or warn you when you install it. Here’s a yaml sample using PSA and PSP.
| Security Policy Level | PSA | PSP |
| Privileged | Privileged namespace | Privileged |
| Baseline | Baseline namespace | Baseline |
| Restricted | Restricted namespace | Restricted |
For more detailed information about PSA, view Microsoft’s Lachlan Evenson’s talk The Hitchhiker's Guide to Pod Security and k8s blog the PodSecurityPolicy: The Historical Context. PSA repository.
Dockershim Has Been Removed Since 1.24
Dockershim has been removed since version 1.24. Are you using containerd in your cluster? Note that EKS will end support in the next release, and that AKS and GKE have been using containerd as the default since v1.19. Below is the current default Kubernetes version based on cloud provider.
| Default version |
||
| EKS |
1.23.7 |
Amazon EKS will be ending support for Dockershim starting with the EKS 1.24. More info about dockershim deprecation |
| AKS |
1.24 |
Kubernetes v1.19 or greater default to containerd for its container runtime. More info about AKS and dockershim |
| GKE |
1.24 |
In GKE version 1.19 and later, the default node image for Linux nodes is Container-Optimized OS with containerd (cos_containerd) |
Ephemeral Containers – Supporting the kubectl debug, this launches an ephemeral container in a running pod, the intention being to observe the state of containers in the pod. For example, because using distroless images do not include a shell or any debugging utilities, it's difficult to troubleshoot. An ephemeral container would be a perfect use case for debug distroless images. Read more in the official k8s documentation.
kubectl debug -it my-distroless --image=busybox:1.28 --target=ephemeral-demo
Cgroup v2 support - Cgroups v2 has many advantages such as adding simplicity within the process hierarchy and imposing resource limitations on rootless containers.
Why is Cgroup v2 important? You can find more about it in the video 5 Years of Cgroup v2: The Future of Linux Resource Control and the article Five Things to Prepare for Cgroup v2 with Kubernetes. Read more in the detailed KEP-2254 enhancement proposal.
Local Ephemeral Storage Capacity Isolation - This supports local ephemeral storage isolation at pod and container levels including request/limit settings. Read more in the official k8s documentation and the enhancement proposal KEP-361.
Port ranges in Network Policy though endPort - In NetworkPolicy, you can target a range of ports instead of a single port. Read more in the official k8s documentation and the enhancement proposal KEP-2079.
CSI Migration - Since the Container Storage Interface (CSI) is GA, the migration target has removed the in-tree volume plugins and has been migrated to out-of-tree CSI drivers. The scaleio, flocker, quobyte and storageos drivers have been removed while GlusterFS and Portworx have been added in version 1.25. For further details about the status for each storage driver, read more in the official k8s documentation.
CRD Validation Expression Language to Beta - Expression language from Google project - CEL can be used to validate custom resources. Read the official k8s documentation.
KMS v2 Improvements - KMS v2alpha1 API has been introduced to add performance, rotation, and observability improvements. Read more about KEP-3299.
Seccomp by Default - Enable the use of RuntimeDefault as the default seccomp profile for all workloads. Read more in the official k8s documentation and the enhancement proposal KEP-3240.
Cleaning up IPTables Chain Ownership - Clean up the IPTables chain ownership tangle between kubelet and kube-proxy. Read more about the enhancement proposal KEP-3178.
- Windows support improved: Windows Operational Readiness - Conformance tests for windows using Containerd
- Kubernetes moved container registry from k8s.gcr.io to registry.k8s.io
- Kube-proxy was migrated to a distroless image. For more details about the PR, read about them here.
Kubernetes v1.25 official announcement here: Kubernetes Version 1.25 blog post and the release notes.

