In just about a week we will be live on stage at BlackHat 2017 with this tersely titled talk: Well that Escalated Quickly! How Abusing Docker API Led to Remote Code Execution Same Origin Bypass and Persistence in the Hypervisor via Shadow Containers, and we are very excited.
In this talk we explore in detail an attack on developers who have Docker installed on their machine. We’ll be showing how it works on Docker for Windows users. The attack endgame is a persistent random code execution within the enterprise’s network, practically undetectable by existing security products from the host point of view.
We will do that by introducing two new forms of attacks: Host Rebinding and Shadow Containers. Host Rebinding is used to bypass the Same Origin Policy of browsers, while Shadow Containers is a persistency technique on the hypervisor running containers. Each of those attacks are useful on their own, while the ‘Host Rebinding’ attack is not even limited to containers environment.
If you think an attack on developers is not a real risk to your organization, think again.
An attack on a container developer has two angles: one is obvious, the other less so. The obvious one is the developer’s level of access to enterprise resources. Developers usually have a relatively high level of access privileges at their workstation, in many cases administrative privileges. For starters, they naturally have access to source code and SCM systems, test databases (which may contain copies of production data), test environments, etc. But in many cases, especially in DevOps environments, they may also have access to production. Developers often need to perform operations which might look malicious, and for that reason security controls may either be turned off, or tuned to ignore these false positives.
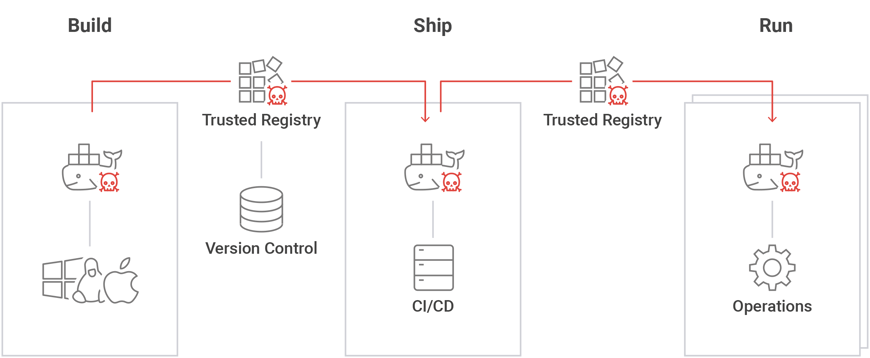
The less obvious angle is that once an attacker gains control of a container developer workstation, he also gains the ability to pollute images built by the container developer. This in turn may enable the attacker to extend his control to production containers. We call this a “Shadow Worm”.
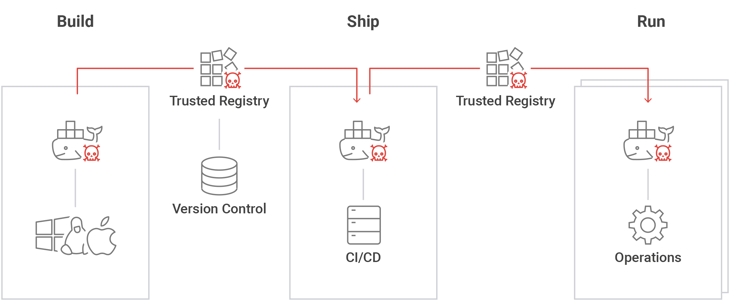
Image 1: ‘Shadow worm’ in the development pipeline
While the attack we show is a complex and multi-stage one, it’s not theoretical and should be treated as a serious risk. Obviously, we will not be leaving you helpless and we’ll finish with discussing how such attack can be mitigated.
Michael and Sagie